KGpg/pt-br: Difference between revisions
Updating to match new version of source page |
Updating to match new version of source page |
||
| Line 20: | Line 20: | ||
== Change your passphrase == | == Change your passphrase == | ||
Should you suspect your passphrase is compromised, you can change this also from the Key Properties dialogue. The <menuchoice>Change Passphrase</menuchoice> button is below <menuchoice>Change Expiration</menuchoice>. | Should you suspect your passphrase is compromised, you can change this also from the '''Key Properties''' dialogue. The <menuchoice>Change Passphrase</menuchoice> button is below <menuchoice>Change Expiration</menuchoice>. | ||
== Revoking a key == | == Revoking a key == | ||
| Line 28: | Line 28: | ||
The revocation signature can be created together with the key. In this | The revocation signature can be created together with the key. In this | ||
case it is stored in a separate file. This file can later be imported into | case it is stored in a separate file. This file can later be imported into | ||
the keyring and is then attached to the key rendering it unusable. {{Warning|1=Please | the keyring and is then attached to the key rendering it unusable. | ||
note that to import this signature to the key no password is required. | |||
Therefore you should store this revokation signature in a safe place, | {{Warning|1=Please note that to import this signature to the key no password is required. Therefore you should store this revokation signature in a safe place, usually one that is different from you key pair. It is a good advise to use a place that is detached from your computer, either copy it to an external storage device like an USB stick or print it out.}} | ||
usually one that is different from you key pair. It is a good advise to | |||
use a place that is detached from your computer, either copy it to an | |||
external storage device like an USB stick or print it out.}} | |||
If you have not created such a detached revocation on key creation you can | If you have not created such a detached revocation on key creation you can | ||
Revision as of 16:53, 14 September 2011
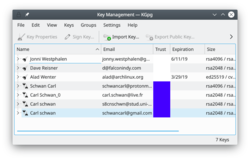 |
O 'KGpg fornece uma interface gráfica para os comandos do gpg' |
O GnuPG criptografa e decriptografa suas mensagens de correio e arquivos selecionados. Existem muitas opções de linha de comando para fazer isto. Com o KGpg a ansiedade é descartada - você não precisa mais decorar qualquer comando. O KGpg pode auxiliá-lo a configurar e gerenciar suas chaves, importar e exportar chaves, ver assinaturas, status de confiança e datas de expiração das chaves. De fato, praticamente tudo de que você precisa é fornecido pelo KGpg. Um assistente é disponibilizado para auxiliá-lo a configurar suas chaves.
O KGpg é integrado ao Konqueror e o Dolphin, onde um menu de contexto permite que você opte por criptografar um arquivo, com ou sem assinatura.
 |
 |
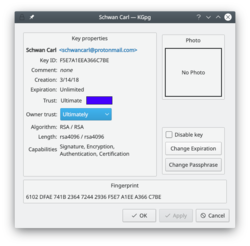
Extending the life of your keys
As you can see in the image above, you can extend the life of your keys using the button. Simply choose the new date from the popup calendar. To do this, however, you must have access to the private key and its pass-phrase. Without them you can do nothing.
Change your passphrase
Should you suspect your passphrase is compromised, you can change this also from the Key Properties dialogue. The button is below .
Revoking a key
If you lose your private key or think it has been compromised in some way you need to revoke it. To reliably render a key unusable you need to revoke it. Revoking is done by adding a special revocation signature to the key.
The revocation signature can be created together with the key. In this case it is stored in a separate file. This file can later be imported into the keyring and is then attached to the key rendering it unusable.
If you have not created such a detached revocation on key creation you can
create such a revocation signature at any time choosing , optionally importing it to your keyring immediately.

Tip

Tip
Um manual totalmente ilustrado lhe ajudará em cada detalhe.
Se você não estiver condições de verificar fisicamente a identidade de seus contatos, você deve ler a seção de assinatura de chaves que explica os benefícios da assinatura local.


