KGpg/da: Difference between revisions
Updating to match new version of source page |
Importing a new version from external source |
||
| Line 14: | Line 14: | ||
|} | |} | ||
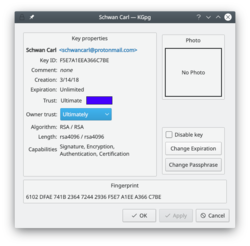
== | == Forlæng dine nøglers levetid == | ||
As you can see in the image above, you can extend the life of your keys using the <menuchoice>Change Expiration</menuchoice> button. Simply choose the new date from the popup calendar. To do this, however, you must have access to the private key and its pass-phrase. Without them you can do nothing. | As you can see in the image above, you can extend the life of your keys using the <menuchoice>Change Expiration</menuchoice> button. Simply choose the new date from the popup calendar. To do this, however, you must have access to the private key and its pass-phrase. Without them you can do nothing. | ||
Revision as of 16:50, 14 September 2011
 |
KGpg er en grafisk brugerflade til gpg's kommandoer |
GnuPG krypterer og afkoder dine emails og udvalgte filer. Der er mange muligheder for at gøre dette fra kommandolinjen, men med KGpg bliver det nemmere - du behøver ikke at huske de mange kommandoer. KGpg kan hjælpe dig med at lave og håndtere dine kodenøgler, importere og eksportere nøgler, vise nøglernes signaturer, hvor meget tillid, du kan have til dem og hvornår de udløber. Faktisk kan du gøre alt, hvad du har brug for med KGpg. Der er en dialog til at hjælpe dig med at lave dine nøgler.
KGpg er integreret i Konqueror og Dolphin, hvor du ved hjælp af en højrekliksmenu kan kryptere en fil med eller uden signering.
 |
 |
Forlæng dine nøglers levetid
As you can see in the image above, you can extend the life of your keys using the button. Simply choose the new date from the popup calendar. To do this, however, you must have access to the private key and its pass-phrase. Without them you can do nothing.
Change your passphrase
Should you suspect your passphrase is compromised, you can change this also from the Key Properties dialogue. The button is below .
Revoking a key
If you lose your private key or think it has been compromised in some way you need to revoke it. To reliably render a key unusable you need to revoke it. Revoking is done by adding a special revocation signature to the key.
The revocation signature can be created together with the key. In this case it is stored in a separate file. This file can later be imported into
the keyring and is then attached to the key rendering it unusable.
If you have not created such a detached revocation on key creation you can
create such a revocation signature at any time choosing , optionally importing it to your keyring immediately.

Tip

Tip
En fuldt illustreret manual hjælper dig igennem alle detaljer.
Hvis du ikke har mulighed for personligt at verificere dine kontakters identitet, så er det særlig vigtigt, at du læser afsnittet om nøglesignering, som forklarer fordelene ved lokal-signering.


